JWT Authentication in PHP: A Secure Approach to User Sessions
Authentication is at the heart of any web application. Whether it’s a login system, an e-commerce site, or an API, ensuring that only authorized users gain access is crucial. Traditionally, PHP applications relied on sessions and cookies for authentication. However, with the rise of APIs and distributed systems, a more modern solution has gained popularity: JWT (JSON Web Token) authentication.
1. What is JWT?
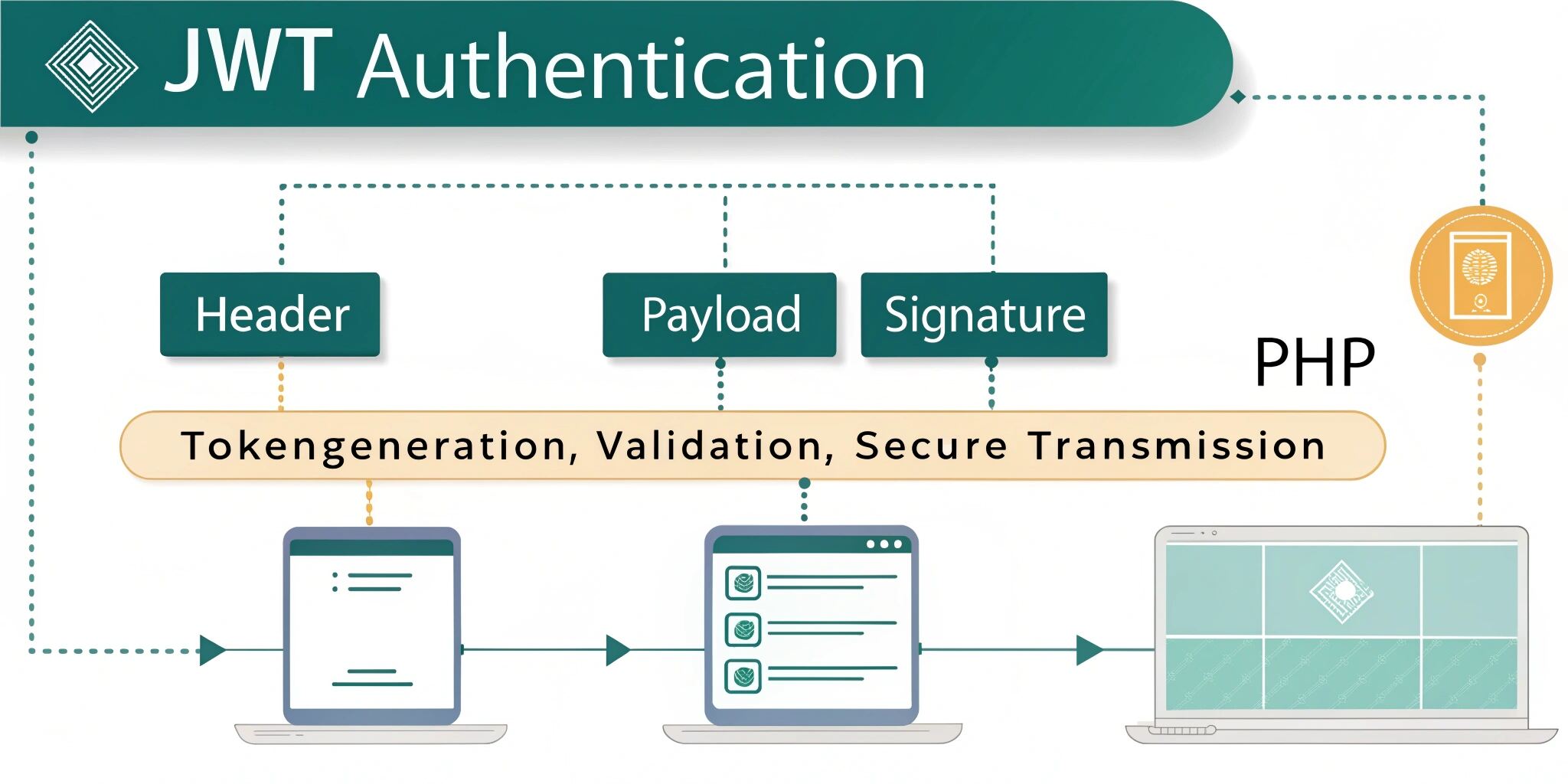
A JSON Web Token (JWT) is a compact, URL-safe token used for securely transmitting information between parties. It is widely used in authentication and authorization systems because it’s lightweight, secure, and works well across different platforms.
A JWT is divided into three parts:
- Header – Contains metadata, such as the type of token and the algorithm used.
- Payload – Holds the actual claims, such as user ID or role.
- Signature – Ensures the token hasn’t been tampered with.
2. Why Use JWT in PHP Applications?
JWT is particularly useful in modern PHP applications because of its benefits:
- Stateless Authentication: Unlike traditional sessions, no server storage is required.
- Cross-Platform Compatibility: Works seamlessly with mobile apps, SPAs (Single Page Applications), and APIs.
- Scalability: Ideal for microservices and distributed architectures.
- Security: Encrypted tokens ensure data integrity and prevent tampering.
3. How JWT Authentication Works in PHP
The JWT authentication flow in PHP can be broken down into these steps:
- User Login – A user enters their credentials (username and password).
- Token Generation – If the credentials are valid, the server generates a JWT and sends it to the client.
- Client Storage – The client stores the token (usually in localStorage or sessionStorage).
- Accessing Resources – For each request, the client sends the JWT in the headers.
- Token Verification – The server verifies the token’s validity and grants or denies access.
This process eliminates the need for traditional PHP session IDs.
4. Real-World Use Cases of JWT in PHP
- API Authentication: Securely grant access to APIs in web or mobile apps.
- Single Sign-On (SSO): Enable login across multiple applications with one token.
- Mobile Applications: Allow apps to authenticate users without managing sessions.
- Role-Based Access Control: Include roles/permissions in the payload to restrict features.
5. Best Practices for JWT in PHP
While JWT is powerful, it must be implemented carefully to ensure security:
- Always use HTTPS to prevent token interception.
- Set a token expiration time to limit risks if tokens are compromised.
- Store sensitive data securely and avoid putting confidential information in the payload.
- Regularly refresh tokens to maintain secure sessions.
- Use strong signing algorithms (e.g., HS256 or RS256).
Conclusion
JWT authentication in PHP provides a modern, secure, and scalable alternative to traditional session-based authentication. By using tokens, developers can streamline user authentication across APIs, web apps, and mobile platforms. As PHP applications grow in complexity, JWT offers a reliable method for maintaining secure user sessions and protecting resources.